About Threat Meter
Continuously view, monitor and improve cyberhealth of your entire ecosystem.
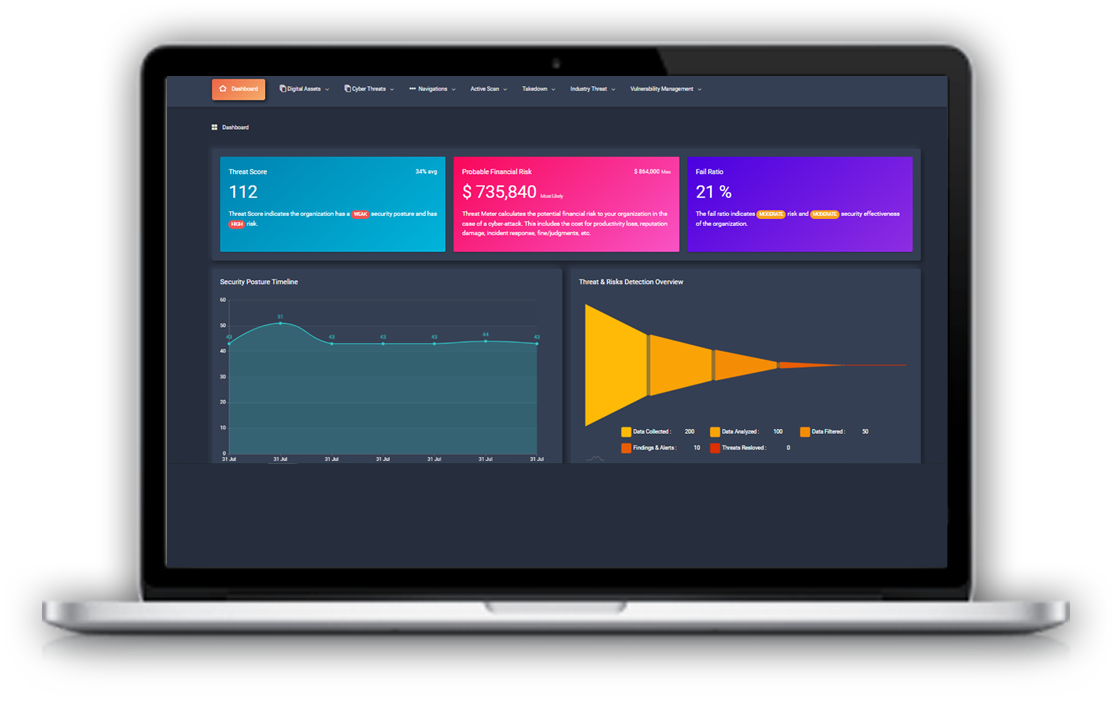
Threat Meter gives you an outside-in view of the security posture of your entire IT infrastructure. Based on the frequency you choose for monitoring, Threat Meter helps you understand how you stack up across various risk categories :
DNS health

Public data leaks

Open ports

SSL health

Outdated patches

Site reputation

IP reputation

Service misconfiguration
Key Features
Driven by AI. Powered by human intuition.
Scan beyond perimeter
Identify and minimize external risks by gaining insights on exploitable weakness, compliance issues, misconfigurations, open ports, etc.
Know MoreManage brand & reputation
Detect and discover impersonating domains, social media accounts, and mobile applications. Takedown before they target the customers or employees.
Know MoreMonitor dark & deep web
Comprehensively monitor surface web, dark and deep web. Track exposed data across online file stores, criminal forums, code repositories, marketplaces, paste sites and other sources.
Know MoreDetect phishing threats
Get the deepest visibility into different phishing threats. Uncover typo squatting domains, phishing pages and takedown them.
Know More
Rogue mobile apps
Actively monitor and hunt down unofficial and rogue mobile applications. Report and takedown them.
Know More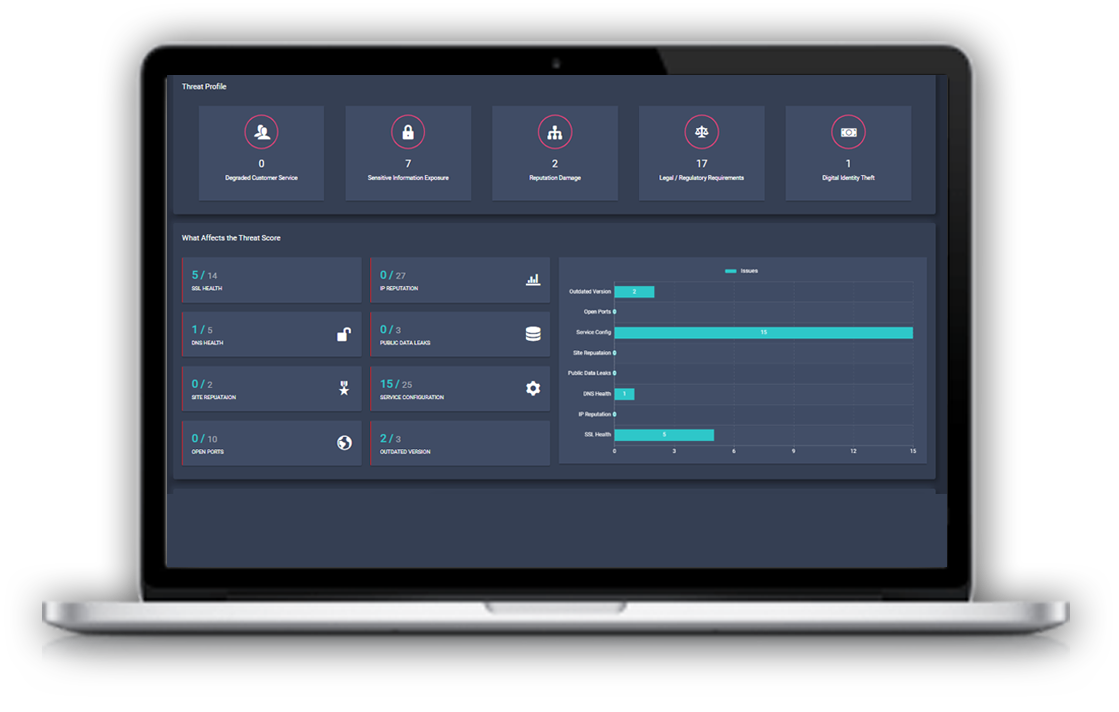
The Threat Meter Advantage
Getting hacked isn’t pleasant. Odds are hackers have already got hold of information about you that they can use to attack you from wherever they are. We’re on your side in this forever war.
Start NowKnow The Key Advantages
SaaS Dashboard

No Installation Required
No Access Required to Assets
Completely Passive and Non Intrusive

Hacker View From Outside
Take Down & Counter-Measure
Clients