How hackers search and hijack sensitive databases?

This will be an exciting blog!
Today we will try to show how easily cyber attackers can gain access to sensitive database. Let’s start.
EXAMPLES OF MANUAL SEARCH
There are two ways to find test subjects.
The first way is take help of existing online services that scan the whole internet and provide us with information.
- Shodan.io
- Fofa.so
- Censys.io
- Zoomeye.org
- Binaryedge.io
- Lampyre.io
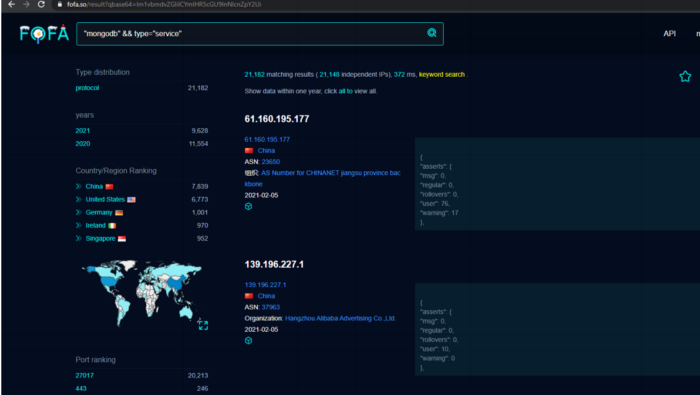
We will not show everything in detail, but will help you with a few interesting examples. Here is a MongoDB search query for the Fofa service.
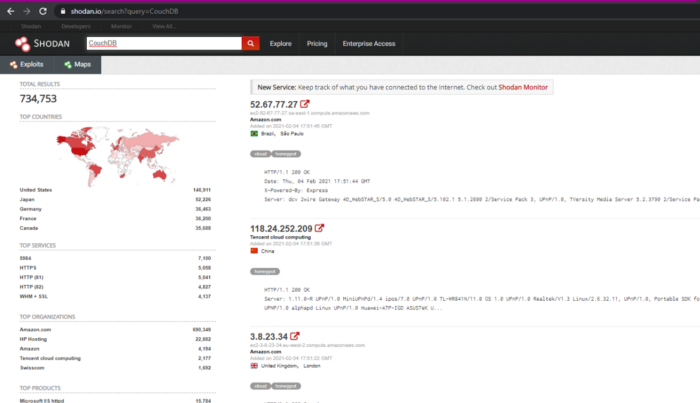
A similar service is shodan.io A request to search for hosts with CouchDB raised here.
A second way is to use advanced scanners.
- Nmap
- Masscan
- Zmap from the Zmap.io utility package
- Sonar project
- Something of its own
Scanning is, of course, manual, but why not use a ready-made dataset? For example, if your VPS provider does not allow you to scan everything at high speed, then these guys have already done everything for you. Almost!
Not many people have heard of Project Sonar. It is a research project that scans services and protocols to gain insight into the global impact of common vulnerabilities. Developed by the company that created the Metasploit Framework. Hopefully, you know about — Rapid7. The collected data is available to the general public for security research.
For Masscan, write the following command to start:
masscan -p9200,9042,5984,27017 52.67.77.27
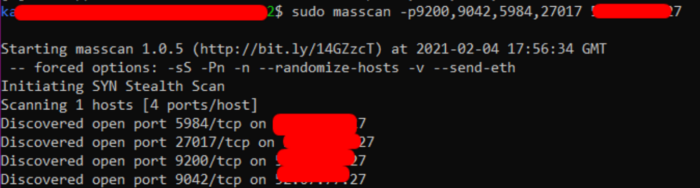
that we have a list of hosts in hand, we can proceed to a detailed check.

Are you aware of your external attack surface and easy-to-exploit available data on internet?
71% of organizations do not have a sufficient understanding of their external attack surface.
Organizations that care to scan beyond their perimeter are not proactive enough in remediation. According to the reports, around 73% of issues are closed or remediated between the first and last scan. And organizations take approximately 86 days to fix them. The rest, 27%, are open flaws, and half of them have been open for 216 days and counting.
Cyber attackers take advantage of such gaps, vulnerable unknown assets, and slow-remediation process.
Recognizing this need, Sumeru’s Threat Meter serves as a unique and powerful external attack surface monitoring tool that can give you the hackers’ view of your organization and helps you to remediate the critical issues to make hackers’ life tougher.
This tool has been deployed across multiple business verticals and businesses which have expanding digital footprint. We are excited to observe the massive difference the Threat Meter is making in their security programs and posture. Know more about Threat Meter here
https://inservice.sumeru.com/threat-meter/